About
岡山大学大学院 自然科学学域 野上保之教授、小寺雄太助教の運営する情報セキュリティ工学研究室(野上・小寺研究室)のホームページです。 暗号・乱数・通信プロトコル・誤り訂正符号など情報社会の安全・安心を実現するための研究、そのための離散数学、C/C++/Java/HDLなどプログラム技術、FPGA・マイクロコンピュータなどハードウェア実装技術などを行っています。 研究室での活動・生活を通して高度な技術を修得し、アクティブに社会で貢献できる人材を育成します。
News & Events
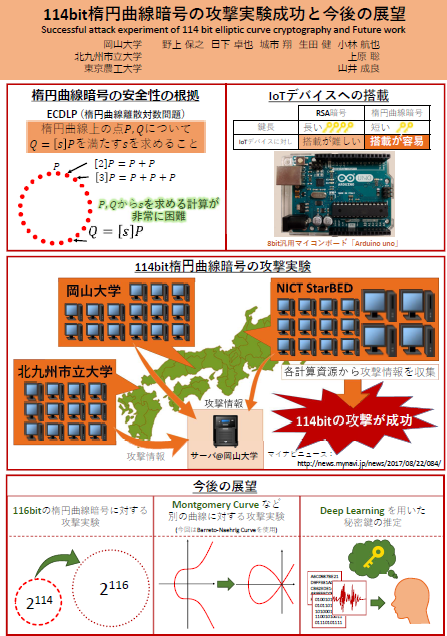
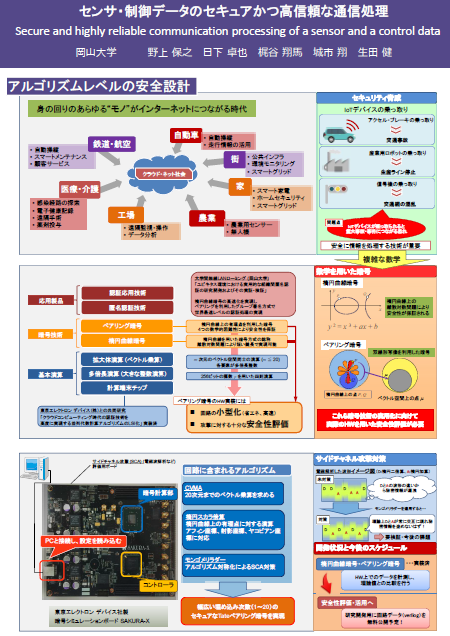
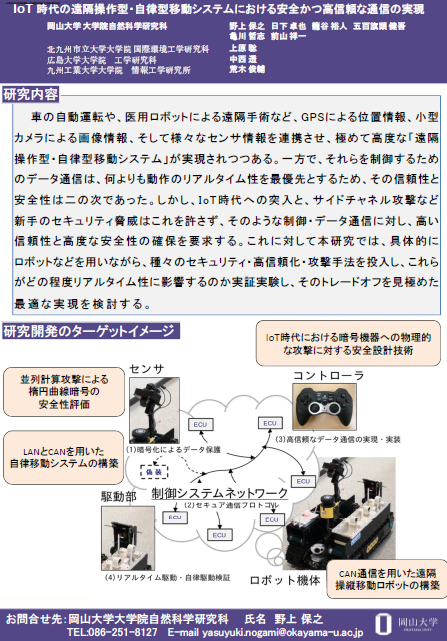
Posters
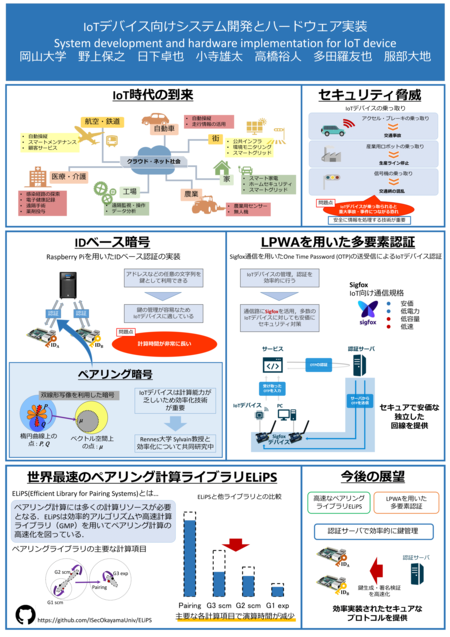
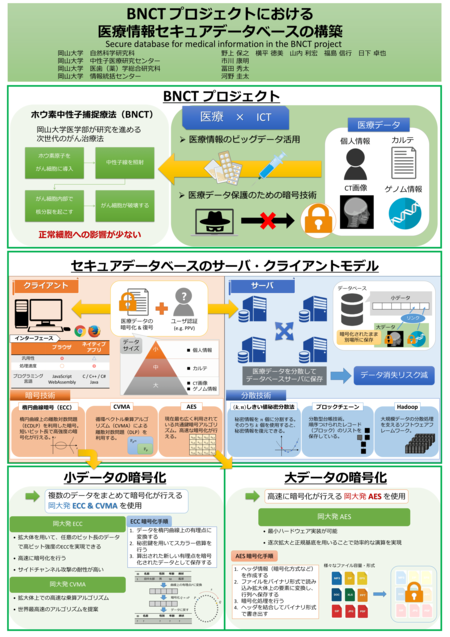
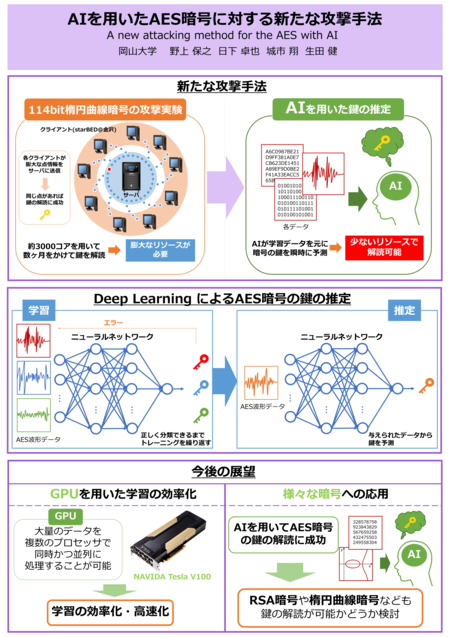
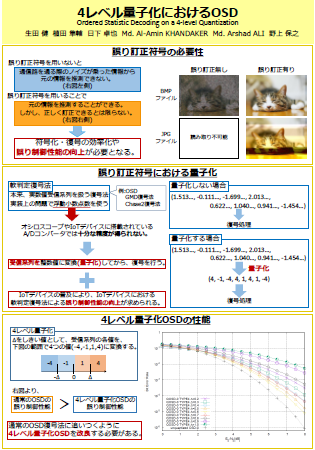
クリックするとPDFを表示します