

Generating higher-degree irreducible polynomials using variable transformations
Determining the trace of an element in extension field
Preparing normal basis
Power residue and non-residue
Testing and generating primitive polynomials
Basis efficient for fast implementation
Fast and compact multiplication algorithm over extension field and its software/hardware implementation
Fast exponentiation and square root calculation over extension field
Constructing self-dual normal basis in aribitrary extension field systematically
Basic translation between isomorphic extension fields
Successive extension with composite extension degree
Fast implementation of definition field of cryptographic applications
Constructing secure elliptic curves and hyperelliptic curves
Checking the parity of (#E-1)/2 and (#Jc-1)/2
Fast implementation of XTR-based cryptographies
Public-key cryptography that can scalably change its key-length
Pairing-based cryptographies with Weil, Tate, and Ate pairing
Generating prime order elliptic curves with quadratic or cubic twisted curves
Fast scalar multiplication over twisted elliptic curve
Generating pairing-friendly curves
Hyperelliptc curve cryptography
Currently, security is necessary for us to protect our personal information from a vicious attacker. Recently, Elliptic Curve Cryptography(ECC) is attracting attention as a stronger security than before. The security of ECC is based on the computational difficulty of the Elliptic Curve Discrete Logarithm Problem(ECDLP). It depends on the computer’s performance and the number of computers that can be parallelized. As an example, 112-bit ECDLP was actually solved by a cluster of more than 200 PlayStation 3 game consoles for half a year and it is the largest size of ECDLP ever solved. The threat of parallel attacks has increased because advanced information and communication technologies facilitate parallel computing through the internet. It is crucially important to verify the practical security against parallel attacks. Therefore, We aim to evaluate the security of ECDLP by attacking to it actually. Now, we attack to the 114-bit ECDLP by about 200 computers (starBED) which provided from NICT.
IoT (Internet of things) / IoE (Internet of Everything) era has come. Everything will be connected to the Internet and various types of information are transmitted between not only computers but also small devices. Of course, it includes very sensitive and private information such as ID, birthday, credit card number, and so on. PC can efficiently and securely carry out encryption and decryption for the secure transmission; however, it is very heavy for small devices such as IC card and microcontrollers, namely IoT devices.
Pairings on elliptic curves is a relatively new and active area of research in cryptography which is often known as Pairing-based Crypto (PBC). By using some certain mathematics, pairing maps a pair of points on an elliptic curve into the multiplicative group of a finite field. Such technique yields several new cryptographic protocols that had not previously been feasible.
One of the widely known protocols realized by PBC is identity-based encryption (IBE), which overcomes the need of knowing the receivers public key in prior of sending the secure message.Another innovative application of PBC is functional encryption which allows anyone who possesses a particular set of attributes defined during encryption stage, can decrypt the message. It is also known as attribute-based encryption (ABE). More and more novel ideas are in the pipeline from the academia and industry who are involved in research of PBC. Therefore we can say, pairing-based cryptography is now in the frontline of next generation of security.
The Secure Database targets big data that is one of the Information technology attracting the most attention now, because more information will have been rapidly uploaded on the Internet. It reduce the risk of leakage the data such as personal information, posts on SNS or even a log of the air temperature in a room, regardless the type of data.
We use a unique block cipher as SSE (Symmetric Searchable Encryption) and process the data just as it is encrypted. It means that it doesn’t need to be decrypted each time we operate the database, so we can manage the data in better security.
The time for replacing the conventional computational system with the quantum computer is coming in the near future. It is known that the Shor’s algorithm with quantum computer enables us to solve the mathematical hardness such as prime factorization and Discrete Logarithm Problem. In other words, the conventional public key cryptographies, for example, RSA and Elliptic Curve Cryptography, will be broken by the quantum computer in polynomial time. In this context, a lattice-based cryptography called NTRU has been paid much attentions as post-quantum cryptography. It is constructed on the shortest vector problems and is able to encrypt data much faster than RSA. In addition, it can use for making a searchable cryptosystem which allows us to find the data without decryption. Such kinds of mathematical background and applications are investigated in our lab.
Currently, security is necessary for us to protect our personal information from a vicious attacker. Recently, Elliptic Curve Cryptography(ECC) is attracting attention as a stronger security than before. The security of ECC is based on the computational difficulty of the Elliptic Curve Discrete Logarithm Problem(ECDLP). It depends on the computer’s performance and the number of computers that can be parallelized. As an example, 112-bit ECDLP was actually solved by a cluster of more than 200 PlayStation 3 game consoles for half a year and it is the largest size of ECDLP ever solved. The threat of parallel attacks has increased because advanced information and communication technologies facilitate parallel computing through the internet. It is crucially important to verify the practical security against parallel attacks. Therefore, We aim to evaluate the security of ECDLP by attacking to it actually. Now, we attack to the 114-bit ECDLP by about 200 computers (starBED) which provided from NICT.
| Associate Editor | International Journal of Network and Computing |
|---|---|
| Associate Editor, 2016-2017 | IEICE Trans. Special Issue of SITA |
| Associate Editor, 2016-2017 | IEICE Trans. Special issue of SCIS |
| Session Chair | ICCE-TW2017 Organized |
| Program Committee Member, 2015-2017 | International conference DSD, AHSA |
| WICS Co-Chair, 2015-2017 | International conference CANDAR |
| Co-Secretary | International symposium ISITA2018 |
| Technical Program Committee | International Symposium ISITA2016. |
|---|---|
| Invited Lecture "Cryptographic Techniques in IoT Era" | IEICE Society symposium |
| Core Member Meeting | A member of SMA and NICT:StarBED |
| Advisor | Domestic symposium SITA2017 |
| A member of Chugoku IoT Research Meeting | |
| technical program committee, organizer and chair of special session "Advanced cryptography and its applications" | International conference ICCE-TW |
| Invited Lecturer "Cryptographic Techniques in IoT Era" | IEICE Society symposium. |
| A member of core member meeting | SMA and NICT:StarBED |
| Special lecture at 91岡山県技術・市場交流プラザ | |
| Special lecture@新技術協会 "Cryptographic Techniques in IoT Era" | |
| A member of Chugoku IoT Research Meeting | |
| Technical Program Committee, Organizer and Chair of Special Session "Advanced cryptography and its applications | International conference ICCE-TW |
| Committee Member | IEICE Technical group of Hardware Security |
| Associate editor | IEICE Trans. special issue of IWSDA. |
| Advisor | Domestic symposium SITA2017 |

Advances in cybersecurity technology are important to meet the challenges of ensuring the safety and social acceptably of the proliferation of technology based cloud computing and internet of things (IoT).
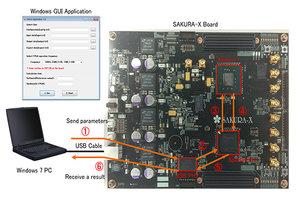
Information security technology is necessary for the Cloud and IoT era. Particularly, public key cryptography such as RSA cryptography and elliptic curve cryptography plays an important role since it enables digital authentications for users and devices.

Dr. Yasuyuki Nogami and his colleagues’ research group of Okayama University has developed a noble secure cryptoprocessor that a security level can be changed freely.
Security of information communication supported by mathematics by Professor Yasuyuki. This video is only available in Japanese language with English subtitle.
Information security technology based on cryptography is indispensable in the current information society centered on the Internet. While there are mathematical difficulties that many computing machines can not solve, we introduce that simple mathematics such as integer arithmetic and prime numbers are active.
Tsushima-naka 3-1-1, Kita-ku, Okayama 700-8530, Japan.
Faculty of Engineering, Building 03 (2nd floor),
Okayama University.